Quick review on my career after learning PowerShell
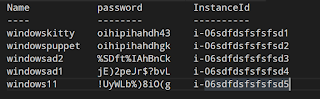
I have been an operator through our my IT career, clicking through the software install, user/ machine provisioning, and checking logs until I learned PowerShell. At first, I started scripting many of the repetitive tasks, and then some complex ones. They generated regular Active Directory/ file system/ Exchange reporting, scanned for cryptolocker affected files in file shares, and audited Exchange user attributes for the entire company. Things got wild after having a bunch of PowerShell scripts laying around in my local folders. Now I look back, it seems the path evolved so naturally. I needed a way to manage the PowerShell scripts and their history safely. So I started using Git. I wanted to work with others on my team and we had peer reviews. Spinning up VMs/ Cloud instances were then became bottlenecks in the workflow so configuration management and Infrastructure as code were embraced. Secret management, logging and monitoring, automated backup and recovery.... more and more w